With so many employees working on a remote basis for much of the work week, it has become essential for organizations to find improved, more modern, and cost-efficient ways to protect their networks and data.
In line with this requirement, organizations are investing in virtual private networks, or VPNs.
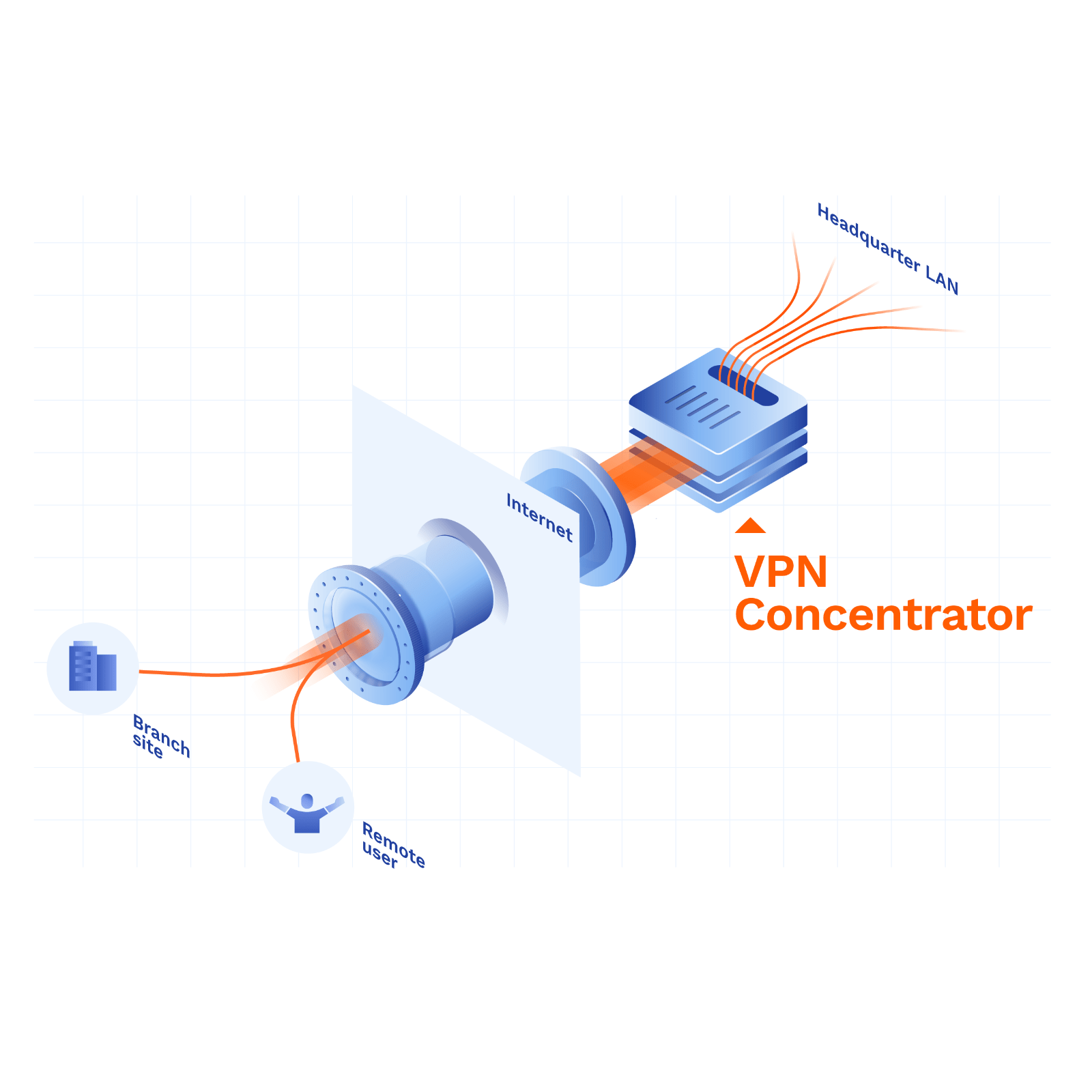
At the heart of the VPN sits the VPN concentrator, VPN gateway, or VPN router.
In this article, we will take a look at exactly what a VPN concentrator is. We will also explain how it works and point out the benefits that it holds for your business.
Table of contents
What Is a VPN Concentrator?
A VPN concentrator is a dedicated network device that provides secure connections between remote users and a company network.
VPN concentrators tend to be enterprise-grade devices capable of handling a large number of simultaneous Internet connections. They can be deployed either as an on-site piece of hardware, or virtually via the cloud.
You can think of a VPN concentrator as a scaled-up VPN router with a few bells and whistles attached. You may also think of it as another name for a VPN gateway that has been marketed as a stand-alone product.
A VPN concentrator is able to serve thousands of users at the same time. You can use them to protect communications across a wide range of devices, between remote employees or remote clients.
What Is a VPN Router and a VPN Gateway?
A VPN router is a routing device with VPN software installed on it that enables network communications within a virtual private network, or VPN environment.
A VPN gateway is a broader term for the central node of a VPN that encompasses VPN concentrators and cloud-based VPN gateways.
What Does a VPN Concentrator Do?
The main purpose of a VPN concentrator is to provide secure remote access over the public Internet or untrusted networks, via a secure tunnel or secure Internet connection.
Multiple encrypted VPN tunnels protect the movement of data from one network to another.
In the language of VPN connections, this is called a point-to-site VPN.
In companies with several remote locations, individual local VPN concentrators can be interconnected via multiple encrypted VPN tunnels, or site-to-site tunnels.
VPN concentrators perform other tasks as well, such as:
- User authentication – Only verified company employees are granted access with assigned privileges. This prevents unauthorized access to the company network and protects company data from theft and misuse.
- Traffic encryption – VPN concentrators establish multiple end-to-end encrypted connections (multiple VPN tunnels), which conceal data during transit over the Internet and protect this data from interception.
- IP address assignment – Users are assigned IP addresses. These provide secure remote access to cloud systems (IP whitelisting).
With proper configuration, a VPN concentrator can fulfill several advanced functions, including:
- Providing secure remote access – The primary use case is to provide remote access to remote employees with the same level of security and privacy as they would enjoy on the company LAN.
- Allowing network segmentation – VPN concentrators capable of assigning privileges can segment the network by limiting the number of privileges a user receives. If an attacker manages to penetrate the network, the damage they inflict will be compartmentalized to a limited number of virtual or local systems.
- Performing identity obfuscation – Encrypted tunnels hide metadata about the communicating parties, such as IP addresses or port numbers. This conceals the user’s activity on the Internet and protects their data from interception.
- Managing application access – Modern VPN concentrators allow remote users to safely access SaaS applications by establishing a private tunnel between them and the application.
The Benefits of Using a VPN Concentrator
VPN concentrators provide several benefits when it comes to VPN connections. These include:
- High workloads – VPN concentrators are robust stand-alone virtual or hardware devices that are capable of handling hundreds of parallel tunnels.
- Central administration – VPN concentrators provide for easier central management of secure VPN connections.
- Access control – VPN concentrators allow you to restrict user access to selected systems based on attributes or roles.
The Drawbacks of a VPN Concentrator
Although they offer some outstanding benefits, VPN concentrators aren’t ideal for every organization. Some of their downsides include:
- High initial cost – Hardware VPN concentrators tend to come with an enterprise-grade price tag that smaller companies cannot afford.
- Lack of scalability – If you have a large number of remote workers, you may run out of bandwidth to provide a smooth enough service for all of them. In addition, hardware VPN concentrators have a performance ceiling that can only be increased by deploying additional VPN concentrators.
- Management complexity – Configuring a VPN concentrator requires a trained network engineer in order to provide smooth remote access to all relevant networks and systems, as well as to ensure the VPN fits in with the rest of the organization’s security ecosystem.
How a VPN Concentrator Works
Before any data passes between the company network and the user, the VPN concentrator creates an encrypted, secure tunnel. It can use several VPN protocols to do this, often more than one at a time.
A VPN protocol is a set of rules that determines how data moves between a device and a VPN server.
For example, a VPN protocol decides how a piece of data will be encrypted and sent from the user's device to the VPN server.
Some examples of VPN protocols include:
- OpenVPN
- Secure socket tunneling protocol (SSTP)
- Internet key exchange version 2 (IKEv2)
- Wireguard
- Point-to-point tunneling protocol (PPTP)
- Layer 2 tunneling protocol (L2TP)
The traffic that is sent through this tunnel is encrypted before departure and decrypted upon arrival.

Alternatives to a VPN Concentrator
VPN router
A VPN router provides similar functionality to a VPN concentrator, but with fewer features and at a smaller scale. It may be a good alternative for companies with fewer remote workers and a smaller budget.
On the other hand, the configuration complexity is still very high, if not higher, as you may need to configure each of the VPN clients individually.
Business cloud VPN
A cloud-delivered business VPN provides a remote-access service identical to a VPN concentrator, but without any of the downsides that we have mentioned.
The function of the VPN concentrator is taken over by a cloud-based VPN gateway. This is a virtual device that handles site-to-site and point-to-site tunneled connections in a highly scalable way.
Being SaaS-delivered, business cloud VPNs are best suited for small and medium-sized businesses for these reasons:
- The price matches the performance, so companies only pay more when they use more.
- A cloud VPN scales easily according to changing needs.
- A cloud VPN is quick and easy to deploy.
- The administration overhead rests with the service provider, which eliminates management complexity for the business.
At GoodAccess we provide you with the perfect business cloud VPN solution. You can enable zero trust global remote access to protect your communications wherever your users may be.
Setup is quick and easy—you don’t need any technical expertise. Create your free account now and get all our premium features for 14 days—no credit card required.
Maintaining Solid Security via a VPN Concentrator
A good network security system includes multiple components, of which VPNs are just one.
It is essential to take a critical view of cybersecurity in your business. Malware and spyware are prevalent today, so the risk of losing sensitive company information and personal data is high.
Data breaches have cost companies thousands and resulted in serious legal consequences due to the loss of sensitive data.
A virtual VPN concentrator is an effective way to protect data from interception. It helps you manage your information security risk successfully.
In Summary
VPN concentrators are reliable, high-performance solutions for securing remote access for a large number of workers, or users.
They ensure you are able to protect your business from serious data breaches, and help you isolate threats in your data network.
Legacy hardware VPN concentrators require serious financial investment and know-how, which means they are more suited to large enterprises.
Small and medium businesses will benefit greatly from the use of virtual concentrators (gateways) that come with business cloud VPNs. SaaS-delivered VPN services scale easily according to your business growth and user requirements. This reduces the complexity and cost of securing your network from data breaches.
Our cloud-based VPN deploys within 10 minutes and is an excellent way to ensure a fast, affordable, and scalable means to secure your network.
Create your free account and enjoy the benefits of your new cloud VPN today.